Summary
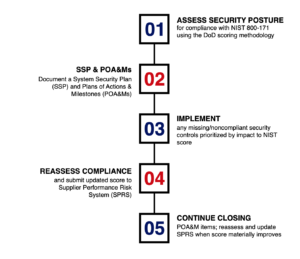
There is growing recognition within the US government that the cybersecurity of the supply chain is a national defense priority. If your company does business with the Department of Defense (DoD) and you anticipate new contract awards, tasks, or option awards on existing contracts anytime after November 30, 2020, you will need to ensure that both your company and your suppliers undergo a NIST 800-171 assessment and report the compliance score to the DoD. Until addressed, this represents a high risk to any organization for whom business with the DoD represents a significant portion of annual revenue.
Background
The DoD’s Interim Rule for its CMMC program plan was published on September 30. Effective November 30, 2020, all DoD contractors (prime and subcontractor) need to report their compliance with the security controls in NIST SP 800-171. The interim rule puts a new assessment and reporting system in place that will verify compliance prior to contract award. Contractors cannot be awarded contracts or award subcontracts unless they and their relevant subcontractors have each performed a NIST 800-171 basic assessment within the last three years and reported those results to the DoD’s Supplier Performance Risk System (SPRS).
Scoring NIST 800-171 Compliance
The interim rule defines a specific scoring methodology that uses a 110-point, weighted scoring system to quantify the extent to which a contractor or offeror has implemented the NIST 800-171 security controls. An information security system that fully implements all 110 NIST 800-171 security controls will have a score of 110. For each unimplemented requirement, 1, 3 or 5 points are subtracted (depending on the control’s importance) out of a total point value of 313. Partial implementation is generally not credited, although two requirements do include built-in scoring for partial implementation. And yes, it’s possible to have a negative score.
Basic assessments are conducted using NIST SP 800–171A, Assessing Security Requirements for Controlled Unclassified Information, as well as Section 5 and Annex A of v1.2.1 of the DOD Assessment Methodology. The DoD scoring methodology assigns greater points to requirements that “have more impact on the security of the network and its data than others.” For instance, security controls designed to “limit system access to authorized users” are critical to protecting information systems, and failing to implement those controls will limit the effectiveness of other controls. Accordingly, they are worth more points than other less critical controls.
The Takeaway
The weighting accorded to each of the security controls provides guidance on how an organization seeking to move the needle on their current cybersecurity posture (and hence, their NIST assessment score) should prioritize their near-term efforts ahead of the implementation deadline. Rather than opening up NIST 800-171 and working from first to last of its 110 requirements, we’re recommending that clients use a targeted approach which focuses on the high impact requirements first.

Those with the DFARS 252.204-7012 clause in current or anticipated contracts, tasks, or options awards need to begin their assessment process immediately. Evaluating all 110 controls will take time. This will also allow the controls to gain maturity in your organization, a requirement to meet the CMMC maturity requirements which are being rolled out in the near future.
Download our 7 Immediately Actionable Ways to Improve Your NIST Assessment Score, which includes a list of resources that will help you jumpstart your efforts to improve your security posture and boost your NIST assessment score as a result.