Background
There is growing recognition within the US government that the cybersecurity of the supply chain is a national defense priority. In response the DoD is rolling out the Cybersecurity Maturity Model Certification (CMMC), a new framework for managing information security risks in the US defense supply chain. Under the current paradigm, contractors that handle “Covered Defense Information” must self-attest to providing “adequate security” to protect that information, but are allowed to work toward implementing the 110 security controls in NIST SP 800-171 over time so long as the plans for doing so are appropriately documented. Unfortunately, self-certification is not working. Anyone following the news is aware that DoD contractors continue to be successfully targeted by cyber adversaries because they haven’t fully secured their networks.
The CMMC Framework
Not only does the new CMMC model mandate additional security controls beyond NIST 800-171 (depending on the level of sensitivity assigned to the procurement), but contractors must be in full compliance with each control before receiving contract Authorization to Proceed. A plan to mitigate a risk, called a Plan of Actions and Milestones (POA&M) under 800-171, will no longer be an acceptable alternative. To achieve certification, all required practices and processes at the targeted CMMC maturity level must be implemented and actively used. And due to the mediocre results of the self-attestation approach, contractors will no longer be able to self-certify compliance. Instead, a verification component has been added and contractors will undergo a certification process via an assessment by accredited third party auditors.
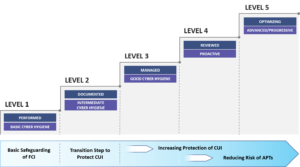
The CMMC model defines five certification levels that reflect the maturity and reliability of a company’s cybersecurity infrastructure to safeguard sensitive government information on their information systems. For each CMMC level, the associated controls and processes should reduce risk against a specific set of cyber threats. As seen below, to be certified as a Level 1 supplier contractors are only required to perform – even in an ad hoc manner – the practices outlined in the CMMC framework for protecting federal contract information (FCI). At Level 3, the organization should be managing their compliance with the necessary processes and resources in place to protect Controlled Unclassified Information (CUI), while Level 5 requires ongoing, proactive cybersecurity controls to be in place.
Preparing for Level 1 Certification
The focus of this and subsequent articles in the series will be to explore what it takes to achieve CMMC Level 1 compliance, which can be summarized as “basic cyber hygiene”. It is intended to be achievable for small businesses, and consists of fundamental cybersecurity practices such as access control, firewalling, anti-malware, physical protection, and sanitizing data from devices or media when it is no longer needed. We assume that as a DoD contractor (either prime or sub) you have determined that you need to achieve at least CMMC Level 1 certification, and are interested in learning more about what compliance entails. This series is primarily intended to aid small and medium-sized businesses (SMBs), many of which have limited resources and expertise whereas large DoD contractors presumably have dedicated security and IT resources. Unless their business is involved with technology, one of the last things SMBs are likely to think about is cybersecurity, and this leaves them vulnerable.
Level 1 compliance requires a company to demonstrate it has implemented the 17 practices that correspond to the basic safeguarding requirements from the Federal Acquisition Regulation (FAR) 48 CFR 52.204-21, “Basic Safeguarding of Covered Contractor Information Systems”. While some controls can be addressed by relatively simple updates to policies and procedures, or minor adjustments to configuration settings and network architecture, others will require an investment in technology or changes to business practices. Some of the bigger challenges you should prepare to encounter include encryption of data (at rest and in transit); multi-factor authentication; audit logs and activity reviews; and mobile device policies.
You Can Do This
For a small business this may sound daunting, but do not be intimidated by the challenge of becoming compliant… the best way to eat an elephant is one bite at a time, and in future articles we will explore what is required for an organization to achieve compliance to each of the 17 practices within CMMC Level 1. The good news is that the Level 1 requirements actually get easier the smaller your company is. And as always, if you have questions related to CMMC or are interested in a readiness assessment, we have the expertise to help.

